Secure Your Future: Protect What Matters Most
AUDITS & ASSESSMENTS
Navigating Complexity with Compliance Audits and Assessments
Compliance isn't just a requirement - it's a commitment to accountability and ethical operations.


Understand the compliance landscape requirements
Comprehensive Compliance Assessments
Tailored Actionable Recommendations
Streamlined Audit Readiness
Risk-Based Compliance Approach
Cross-Border and Multi-Jurisdictional Expertise
Third-Party Risk Management
Continuous Monitoring and Reporting
GDPR, HIPAA, PCI DSS 4.0, SOC 1 & 2, ISO 27001, CCPA
HITRUST, FedRAMP, NIST CSF
Modernize Your Audits with WIISE
The world of internal and external audits is evolving rapidly, and your business must adapt to stay ahead. At WIISE, we offer forward thinking solutions tailored for modern audit teams. From automation that streamlines repetitive tasks, to advanced analytics that uncover deeper insights, to seamless integration with your existing systems, out tools empower your team to operate smarter, faster, and more effectively.
With WIISE, you're not just keeping pace-you're setting the standard for what a future-ready audit function looks like.
Transfor your audit process today with WIISE!
SOC 2 READINESS
Your Trusted Partner for Holistic Audit & Assessment Solutions
In today's fast-paced digital environment, ensuring the security and compliance of your systems and process is critical to maintaining trust, meeting regulatory requirements, and achieving operational excellence. At WIISE we specialize in providing comprehensive audit readiness and assessment services to help your organization navigate the complexities of frameworks such as SOC 1, SOC 2, ISO 27001, HIPAA, NIST CSF, HITRUST, FedRAMP, and more.
Whether it's securing sensitive information, providing compliance, or improving internal controls, our tailored solutions empower you to identify gaps, mitigate risks, and exceed industry standards.
Why Choose Us?
Expertise Across Frameworks: From SOC reports to ISO certifications, our team of auditors brings unmatched expertise across multiple compliance standards
Tailored Approach: No two organizations are the same. We customize our audits and assessments to address your specific risks and goals
Proactive Risk Management: Identify vulnerabilities and inefficiencies before they escalate into costly issues
End-to-End Support: From initial assessments to final reports, we buide you every step of the way
Efficiency and Precision: Our streamlined process minimizes disruptions, saving you time while delivering actionable insights
Our Services
SOC 1 Audits
Evaluate your internal controls over financial reporting (CFR) for compliance and transparency
Demonstrate to stakeholders that your financial systems are secure and reliable
Provide assurance to customers and partners, improving trust in your organization
SOC 2 Audits
Assess your systems based on Trust Service Criteria: security, availability, processing integrity, confidentiality, and privacy
Demonstrate your commitment to safeguarding sensitive data, essential for cloud service providers and technology companies
SOC 2 certification is a key differentiator in industries like technology, SaaS, and cloud services
Meet regulatory demands as many industries require SOC 2 compliance to satisfy contractual and legal obligations
What We Offer
SOC 2 Readiness Assessment: Assist in designing and implementing controls that align with your business process and SOC 2 requiremens. Develop tailored solutions for critical areas like access control, incident management, and data encryption.
Policy and Procedure Development: Craft customized policies and procedures that align with SOC 2 standards. Ensure documentation meets audit requirements while remaining practical for daily operations.
Audit Preparation and Support: Guide your team through the audit process, from initial scoping to final reporting. Provide mock audits and evidence collection assistance to ensure a seamless experience with your external auditor.
Continuous Compliance Support: Offer ongoing assessments to maintain compliance after certification. Providde tools and guidance to adapt to evolving business needs and regulatory changes.
Automated Compliance Solutions: Integrate cutting-edge tools to streamline monitoring evidence collection, and reporting. Enhance visibility into your compliance status with dashboards and automated alerts.
Our SOC 2 Expertise
Security: Implement robust controls to protect your systems and data against unauthorized access
Availability: Ensure your services are reliable and accessible to meet customer expectations
Processing Integrity: Guarantee that your systems process data accurately and as intended
Confidentiality: Protect sensitive customer information with industry-leading security practices
Privacy: Ensure compliance with privacy principles for collecting, storing and managing personal data


ISO 27001:2022
Our Expertise, Your Assurance
We specialize in ISO 27001:2022 audit readiness, offering tailored, end-to-end services that ensure your organization is fully prepared for certification. Our team of seasoned information security and audit professionals combines technical know-how wiwth strategic insights, enabling you to meet every requirement of ISO 27001:2022 with confidence.
Why ISO 27001:2022 Certification Matters
Win Customer Trust: Assure clients and partners that their data is in safe hands
Regulatory Compliance: Meet stringent regulatory and contractual requirements worldwide
Operational Efficiency: Implement streamlined processes that reduce risks and improve productivity
Market Differentiation: Gain a powerful marketing tool to stand out in competitive markets
What Sets Our Audit Readiness Services Apart?
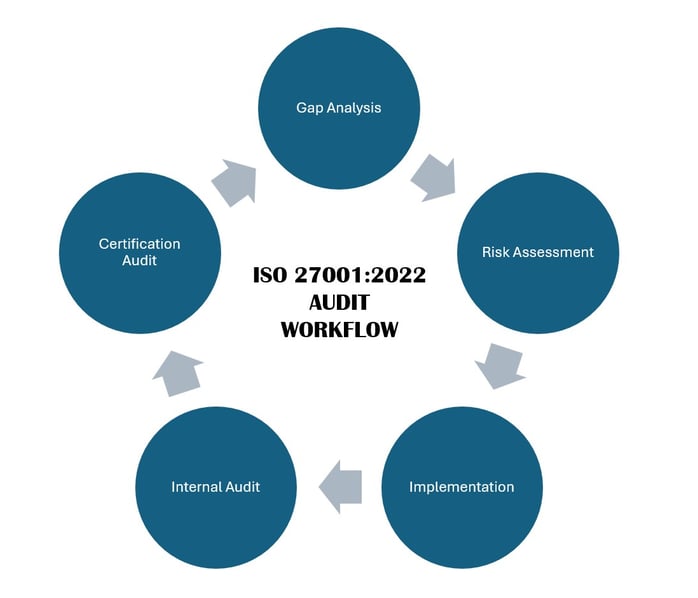
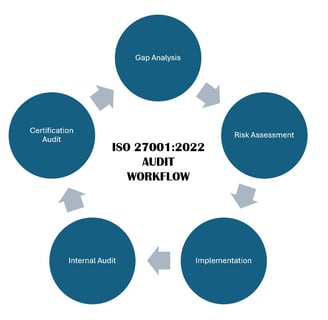
Gap Analysis: A comprehensive review of your current practices to identify areas of non-conformance with ISO 27001:2022 requirements
Customized Roadmap: A tailored action plan detailing step-by-step milestones for achieving certification readiness
Policy and Procedure Development: Creation or enhancement of your Information Security Management System (ISMS) documentation, including policies, risk assessments, and operational controls
Internal Audits: Conducting simulated internal audits to identify and address potential areas of concern before the certification audit
Audit Coaching: Preparation for certification audits with role-based training and mock interviews for stakeholders
Our Proven Process
Assessment: We start with an in-depth review of your organization's existing ISMS and security posture
Strategy: Next, we craft a clear and achievable roadmap tailored to your unique business goals and operational requirements
Implementation: Our experts work alongside your team to implement necessary controls, address gaps, and create robust documentation
Validation: Before the formal certification audit, we conduct internal assessments to ensure your organization is 100% ready to succeed
Certification Support: We support you during the certification audit and beyond, ensuring a seamless journey
ISO 27001:2022 Workflow and Process Documentation
ISO 27001:2022 is the internationally recognized standard for establishing, implementing, maintaining, and cocntinually improving Security Management System (ISMS). To achieve and maintain compliance, organizations must develop comprehensive workflows and process documentation that align with the standard's requirements.
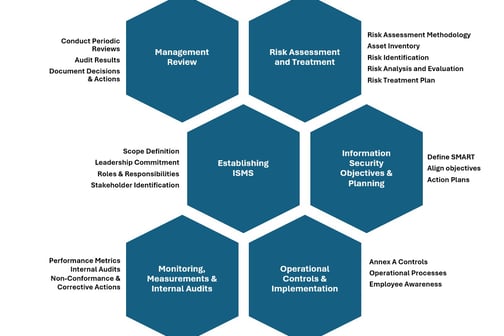
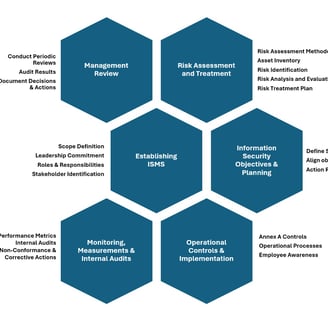
Establishing the ISMS: Define the scope and framework for the ISMS in alignment with organizational goals and regulatory requirements
Scope Definition
Leadership Commitment
Roles and Responsibilities
Stakeholder Identification
Risk Assessment & Treatment: Identify, anaalyze, and mitigate risks to information assets
Risk Assessment Methodology
Asset Inventory
Risk Identification
Risk Analysis and Evaluation
Risk Treatment Plan
Information Security Objectives & Planning: Establish measurable security objectives and a plan to achieve them
Define SMART (Specific, Measurable, Achievable, Relevant, Time-bound) security objectives
Develop detailed plans to achieve each objective, including timelines, responsible parties, and required resources
Operational Controls & Implementation: Implement and document necessary operational processes and controls to mitigate identified risks
Annex A Controls: Review the updated controls from Annex A (93 controls grouped into 4 themes (Organizational, People, Physical, and Technology)
Operational Processes: Develop and document SOPs for critical security processes (e.g., Access control management, Change Management etc.)
Employee Awareness: Implement a documented training program to ensure staff understands security policies and procedures
Monitoring, Measurement, and Internal Audits: Continuously monitor ISMS performance and identify areas of improvement
Performance Metrics: KPIs for ISMS
Internal Audits: Document audit schedules, findings, and corrective actions
Non-Conformance and Corrective Action: Document identified non-conformances and the actions taken to address them
Management Review: Conduct periodic management reviews to ensure ISMS remains effective and aligned with organizational goals
Document inputs such as audit results, risk assessments, incident reports, and performance metrics
Document decisions and actions, including changes to ISMS policies, objectives, and resource allocation
Continual Improvement: Enhance ISMS over time to address emerging risks and opportunities
Develop and document mechanisms for collecting feedback from stakeholders
Create and maintain a plan for continuous improvement initiatives, prioritizing high-impact areas
Certification Audit Preparation: Ensure readiness for the certification audit by external auditors
Pre-Audit Assessment: Conduct a final gap analysis to ensure all ISO 27001:2022 requirements are met
Address any remaining issues or documentation gaps
Organize and ensure accessibility of all required documentation
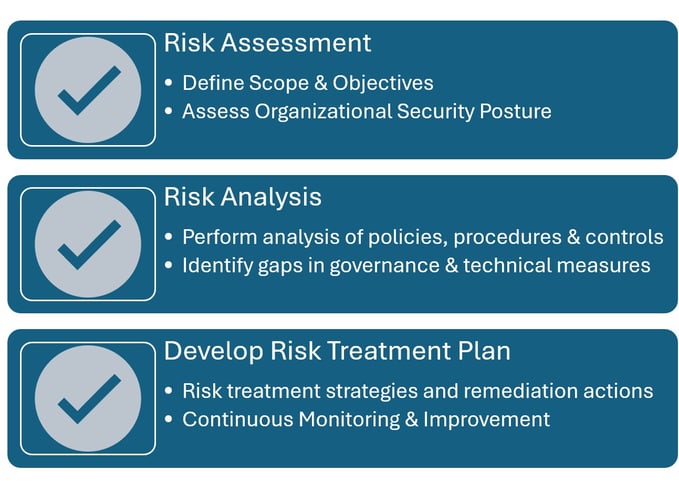
RISK AND COMPLIANCE
Risk Assessment
Wiise conducts a top-down evaluation of your organization's security posture, integrating vulnerability data, security insights from assessments, and findings from questionnaires and interviews. This quantitative analysis identifies key security threats, critical vulnerabilities, and cost effective opportunities to mitigate risk;
Risk Factors (Confidentiality, Integrity, Availability)
Inventory of Critical Assets
Identification and severity of vulnerabilities
Enumeration of Threats
Calculation of Risk
Cost-benefit analysis of risk remediation efforts
Targets:
Sensitive Data
Customer Data, ePHI, Financial Info, SSNs
Critical Systems
Servers, Applications, Databases, Laptops, Firewalls

All rights reserved 2025 © WIISE Consulting.
